 I’m a big believer that time is always your ally. That is my living theology, and when I don’t have the answers I’m seeking, I know that I can go into “waiting mode” and let the answers come to me. In business, time solves many problems. For example, in many cases, if you just wait, often problems will solve themselves.
I’m a big believer that time is always your ally. That is my living theology, and when I don’t have the answers I’m seeking, I know that I can go into “waiting mode” and let the answers come to me. In business, time solves many problems. For example, in many cases, if you just wait, often problems will solve themselves.
So I was waiting for new Windows XP migration messaging from Microsoft, having heard all the regular talking points concerning the April 8, 2014 end-of-support deadline. Let’s just say I thought I’d heard it all until the new “Microsoft Security Intelligence Report, Volume 15” fell into my lap. Stick with me on this one.
During a chit-chat with Holly Stewart, Senior Program Manager in the Microsoft Malware Protection Center, she shared the findings of the latest study, officially titled “The Importance of Using Modern Software to Help Protect against Todays Security Threats.” The insights were impactful.
It all starts with non-NSA surveillance. Microsoft uses readily available and legal approaches to research the type of traffic flowing hither-and-yon to assess IT security threats. For example, billions of Bing search engine-related pages are scanned daily. Microsoft also engages outside vendors that monitor web traffic and the resulting metrics. The bottom line is that operating system features built ten years ago are not an effective defense against modern attacks being launched by opportunistic, motivated and organized hackers. In a previous blog, I highlighted the DEP threat. This new study (version #15) gives DEP a shout out as something that is easily bypassed and then moves onto the “meat.”
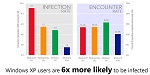
The meat I speak of is that Windows XP users are 6x more likely to be infected. Let me walk you through the attached figure (click the image for a larger version): the left side reflects the successful “infection rate” once someone has knocked on the door and found an opening. The right side reflect door knocks. It’s easy to understand that the infection rate for Windows XP machines is significantly higher than Windows 8.x. Why? It’s back to the ten-year old “building blocks” thesis, such as DEP, whereby hackers easily bypass the Windows XP security model. I get that.
The door knocking scenario, quite frankly, had to be explained twice to me by Stewart. Maybe I was brain dead, but initially I didn’t “get it.” Let me try to explain the encounter rate this way. You are driving in a neighborhood of Windows XP PCs. You randomly knock on door to see if anyone if home. In the case of the Windows XP neighborhood, you knock on 16.3 of the doors in the neighborhood. In the Windows 7 subdivision, you knock on 19.1% of the house doors. The significance is this. Hackers are still very keen on discovering Windows XP machines. Does that make sense?
In my next installment of this series, I dig deeper into “newer is better” looking at a comparison between Internet Explorer (IE) 8 vs. IE10, plus the top three threats facing Windows XP users worldwide.


