Even though most people may not realize it, small and medium businesses are the backbone of the economy. In 2016, there were 28.8 million small businesses in the US, which translates to 99.7% of all American businesses – and in fact, since the 1970s, 66% of total net new jobs are generated by small businesses, which also make for 55% of all jobs in the marketplace. Yet only 50% of those businesses are set to surpass five years and only one third will survive for at least 10 years. This means that SMB owners have to play it smart in order to increase their chances in a highly competitive market – so why not take advantage of free applications that could be ideal for your enterprise?
1. Project Management
One of the most important questions you have to deal with as an SMB is how to deal with managing various projects among the few people that you employ. There are software tools out there that can help make that easier for you, by streamlining communication between team members and allowing you to stay on top of the workflow. Asana, one of the most popular PM apps, is free for the first 15 users, making it great for small businesses. It has a flexible interface and visually documents progress, while it can integrate with services like Evernote, Google Drive, MailChimp, and WordPress.

Source: Pexels
2. Traffic Management
When your SMB has a website – as most businesses today do – then sometimes managing traffic can be daunting. A load balancing tool such as HAProxy (High Availability Proxy) allows you to allocate load across multiple servers and help optimize system performance and speed. HAProxy is a free and open source (FOSS) application– it is included in some Linux distributions, if your system runs on Linux, or it can be downloaded separately. Due to its elaborate nature, though, it also requires IT expertise to set up and maintain – so having the right people on board in-house or hiring outside help is crucial.
3. Productivity
Especially when working in small numbers or when you are freelancing, time can really fly. A good time tracking app can help both you and people on your team stay more focused on the task at hand and spend less time distracted by social media or less important tasks. RescueTime is a time management app that tracks where you allocate your precious time by website and application and allows users to set productivity goals. The basic version is completely free, but if you want features like blocking certain sites or breaking down offline activity, then you’ll have to upgrade to premium for a little extra. RescueTime is flexible across platforms and can be used on Mac, PC, and Linux, but its app is currently only available on Android.

Source: Pexels
4. Team Communication
Besides specialized project management apps, it is nice to have a tool dedicated to internal communication in order to make sure that everyone is up to date and colleagues can get easily in touch when needed. Slack is your best friend – and its basic version is free for an unlimited number of users, although it comes with space and feature limitations. You can create a shared workspace with organized communication channels, customized notifications, searchable messages and mandatory two-factor authentication for extra security.
So if you’d like to increase productivity while on a budget, there is no better way to do it than to look out for these free software tools and choose which one right for your company’s needs.



 such as mission critical data, frequently accessed data, infrequently accessed data and archival data. Each type presents its own unique storage requirements and challenges. The most important type of data among this chunk is mission critical data. This is the type of data that fuels all of the processes of the IT environments of a business. If this data is lost or compromised, the business experiences an outage or downtime.
such as mission critical data, frequently accessed data, infrequently accessed data and archival data. Each type presents its own unique storage requirements and challenges. The most important type of data among this chunk is mission critical data. This is the type of data that fuels all of the processes of the IT environments of a business. If this data is lost or compromised, the business experiences an outage or downtime.





 introducing two innovative new offerings to help in the fight against email scammers. One is a new AI-powered feature designed to improve BEC detection while the other will help IT teams train their employees to spot phishing attacks. It’s one more step towards taking the fight to the bad guys.
introducing two innovative new offerings to help in the fight against email scammers. One is a new AI-powered feature designed to improve BEC detection while the other will help IT teams train their employees to spot phishing attacks. It’s one more step towards taking the fight to the bad guys.




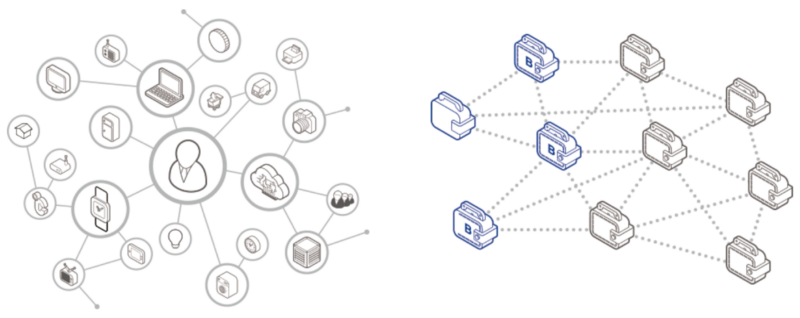
 sensors and telematics embedded in physical objects and linked through wireless networks. As with all new and exciting technologies, it's difficult to separate hype from reality. Certainly the IoT, with its promise of connecting homes and cars, smart grids and smart manufacturing fit into this category. What is different this time around is the convergence of disruptive technologies such as cloud and mobile, shrinking hardware and ubiquitous connectivity, increasing business use cases that are rewriting traditional business rulebook.
sensors and telematics embedded in physical objects and linked through wireless networks. As with all new and exciting technologies, it's difficult to separate hype from reality. Certainly the IoT, with its promise of connecting homes and cars, smart grids and smart manufacturing fit into this category. What is different this time around is the convergence of disruptive technologies such as cloud and mobile, shrinking hardware and ubiquitous connectivity, increasing business use cases that are rewriting traditional business rulebook. The acquisition of Forerunner's Mobilizer and Report Viewer will help Microsoft improve Power BI's reporting capabilities for mobile and web apps.
The acquisition of Forerunner's Mobilizer and Report Viewer will help Microsoft improve Power BI's reporting capabilities for mobile and web apps. cost of ownership. As a managed service provider though, you are in the business of taking on risk for your customers and security is one of the best ways to reduce and mitigate this risk and add value for your customers and for your business.
cost of ownership. As a managed service provider though, you are in the business of taking on risk for your customers and security is one of the best ways to reduce and mitigate this risk and add value for your customers and for your business.



 presentation applications. They’re both solid, useful tools — and both have changed a great deal over the years. Given all their changes, you may want to reconsider what you’re using today.If you’re going to give business presentations, odds are you’ll be choosing between Microsoft PowerPoint and Google Slides, the two best-known presentation applications. They’re both solid, useful tools — and both have changed a great deal over the years. Given all their changes, you may want to reconsider what you’re using today.
presentation applications. They’re both solid, useful tools — and both have changed a great deal over the years. Given all their changes, you may want to reconsider what you’re using today.If you’re going to give business presentations, odds are you’ll be choosing between Microsoft PowerPoint and Google Slides, the two best-known presentation applications. They’re both solid, useful tools — and both have changed a great deal over the years. Given all their changes, you may want to reconsider what you’re using today.
 currently resell IBM technology to shift between engagement models and move up the client value chain
currently resell IBM technology to shift between engagement models and move up the client value chain 
 Partners will operate under the new name of "ZLan Partners, a Sharp IT Company," and we will continue to provide our clients with network design, virtual CIO, cloud, IT security, and managed network services. In addition, we will also be supporting Sharp Business Systems operations in the Chicago, Indianapolis, and Cincinnati areas as well as around the country.
Partners will operate under the new name of "ZLan Partners, a Sharp IT Company," and we will continue to provide our clients with network design, virtual CIO, cloud, IT security, and managed network services. In addition, we will also be supporting Sharp Business Systems operations in the Chicago, Indianapolis, and Cincinnati areas as well as around the country. 

 While this value proposition stands well on its own, it can be even stronger if you think just a bit more broadly. As you know, Microsoft has many partnerships to enhance their offerings, but one in particular is worth noting for taking O365 and SfB to another level.
While this value proposition stands well on its own, it can be even stronger if you think just a bit more broadly. As you know, Microsoft has many partnerships to enhance their offerings, but one in particular is worth noting for taking O365 and SfB to another level.

 can get the foundation to understand the context I’m about to present. Hopefully you’ll note that I’m committed to education both formal and semi-formal (that would be my technology-related certifications). Second, my goal is to lead by example and have your follow along and join the parade. Third, as I’ve opined many times over the past few years. Small Business Server is GONE and it’s time to reinvent ourselves. You’ve done it before; you can do it again.
can get the foundation to understand the context I’m about to present. Hopefully you’ll note that I’m committed to education both formal and semi-formal (that would be my technology-related certifications). Second, my goal is to lead by example and have your follow along and join the parade. Third, as I’ve opined many times over the past few years. Small Business Server is GONE and it’s time to reinvent ourselves. You’ve done it before; you can do it again. an investor-backed RMM ISV.
an investor-backed RMM ISV.
 channel of authorized Audit Guru partners, and includes a robust cloud-based portal that resellers can use to manage the entire GDPR audit and reporting process. MSPs can provide an array of value-added GDPR services built around Audit Guru, which can range from a simple and straight-forward resale of the tool to organizations that have their own internal IT and compliance staff, all the way up to a fully managed, ongoing GDPR Compliance-as-a-Service offering.
channel of authorized Audit Guru partners, and includes a robust cloud-based portal that resellers can use to manage the entire GDPR audit and reporting process. MSPs can provide an array of value-added GDPR services built around Audit Guru, which can range from a simple and straight-forward resale of the tool to organizations that have their own internal IT and compliance staff, all the way up to a fully managed, ongoing GDPR Compliance-as-a-Service offering.