Leading SMB MSP thought leader shares his deep insights into the recently completed CompTIA ChannelCon 2018 conference. Palachuk is seen frequently at leading industry conferences as a speaker and community leader. In my humble opinion, what makes this part of the GeekSpeak is that Karl does a call out to Internet of Things (IoT).
Geek Speak
5 Important Healthcare Cloud Security Factors to Weigh
By Marty Puranki

The healthcare cloud has been growing incredibly, becoming an ever-more-important element of health information technology, or HIT. There are many reasons why the HIT cloud has been becoming more prominent, such as research and development and collaboration.
How is Blockchain Changing the Nature of Trust?

Blockchain has since its beginnings been presented as a very innovative and very promising technology in terms of trust. What is it really? Some recent events raise doubts.
Understand the technology
The blockchain can be classically assimilated to a “big” book of accessible and auditable accounts, which is deployed on the Internet. It is based on a very large number of computing resources distributed around the world, called “nodes”, which participate in the operation of the Blockchain.
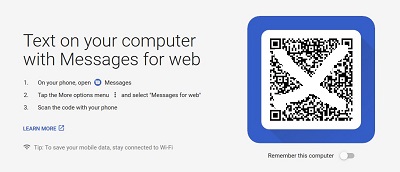
Super Cool Tool – Android Messages for Web
Ya’ just never know when and where you’ll bump into a new geek toy! I unexpectedly learned of one the most cool tools in a longtime from an Alaskan group on Facebook (I grew up in Anchorage). An early childhood friend replied into my unrelated post and that led to a circuitous route to web-based text messaging for Android-based phones. The story gets better in that folks I have now told of this “best kept secret”
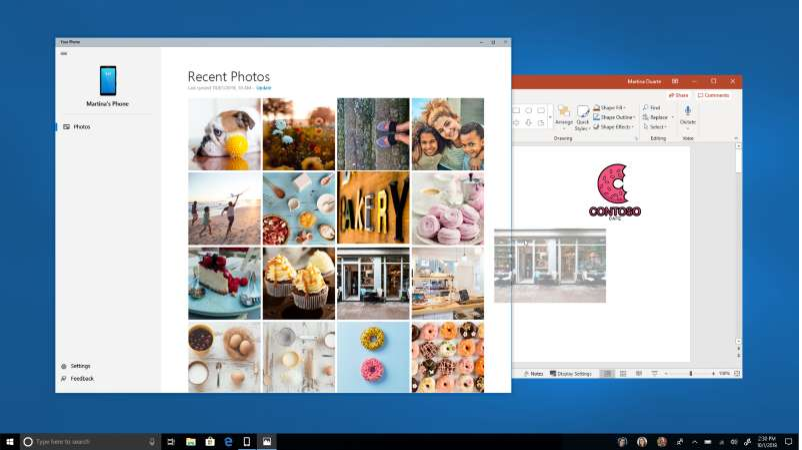
Windows 'Your Phone' app gives you access to Android files on a PC
Mariella Moon
If you have an Android device and happen to be a Windows Insider in the Fast ring, as well, you're among the first people who can take Microsoft's "Your Phone" app for a spin. Microsoft has started testing the experimental application, which gives you easy access to the files on your phone from a Windows 10 PC.
Confirming Website Hack and Repairing It...
What's to be done if you end up being a victim of a website hack or malware attack? How to resolve things when you're at the receiving end of a phishing scam or of any other kind of online fraudulent activity, or if you're receiving spam?
Discussing Proxies, VPNs and the Tor Browser

by: Julia Sowells
In today's world, where internet security is a matter of great concern, one needs to know about terms like Proxies, VPNs and TOR, which are all great tools that help guard one's privacy online and also help ensure better security. The basic thing that these tools provide is anonymity to the user. Though it's one common thing that these three tools provide, there are differences. Let's examine different aspects pertaining to Proxies, VPNs and Tor: